Please don’t forget to subscribe:
Introduction
The topic discussed is servers. I had a question from my student about servers, which was why do we need to have different servers, why not just have one server with everything on it. Good question isn’t it? It is a question this article will attempt to answer.
Servers
A server is a computer program or device that provides a service to another computer program and its user, who is also called the client (Posey, 2023). This happens only when users connect to a server. The tasks done by a server will vary but, they have some functions in common. The client computer makes a request to the appropriate server. The processing of the request is carried out on the server. The server packages the results in a form which is displayed by the client computer’s software (Piper, 2016).
Server Types
There are many different types of servers for different purposes.
Print Servers enable various devices to connect to a printer without installing printer drivers or connecting physically to a printer.
Mail Servers move and store email messages for corporate networks. Browsers are used to place a request to retrieve an email message.
FTP Servers (File Transfer Protocol) keep files within the computer network secure.
Application Servers is where some websites contain programs and scripts. For example: a few websites use MySQL database, which is accessed through application servers. Application servers organise and run web applications. A client’s request from a web browser is sent to application servers.
Network Attached Storage (NAS) is a server that is responsible for storing and sharing files such as music, video and other large files. This does not include websites.
Another type of server is a telnet server which allows computer users to access host computer and perform tasks in the same way as if they’re working on the host.
Web Servers handle the user’s requests and manage the websites. Servers allow users to view HTML pages, CSS stylesheets and other scripts to the user. For example: Apache (open-source). Large files can be hosted and shared using FTP. Internet Information Server (IIS) is one of the most popular web servers from Microsoft that is used to host and provide Internet-based services to ASP.NET and ASP Web applications. A web server is responsible for providing a response to requests that come from users. When a request comes from client to server IIS takes that request from users and process it and send response back to users. Internet Information Server (IIS) has its own ASP.NET Process Engine to handle the ASP.NET request. The way you configure an ASP.NET application depends on what version of IIS the application is running on.
Proxy Servers within a network will filter web requests and block unwanted websites while at the same time improve internet access speeds from a network using what is known as a caching system.
A Terminal Services Server is a powerful server that both stores and runs the application software over the network for client stations. The software is not copied to the client station as it usually combines the additional security features of a proxy server. It often provides a cache of Internet pages, which are pages stored when first accessed so they can be supplied later without the delay of accessing the Internet.
Groupware Servers will allow users to collaborate by using the internet or intranet and work together.
A Fax Server will fax documents out while receiving incoming faxes.
Another type of server is an audio server which brings multimedia to users by streaming videos to users of a particular computer network.
A Virtual Server is a server that shares hardware and software resources with other operating systems (OS). Virtual servers tend to be partitioned inside a real server and is transparent to users, replicating the functionality of a dedicated physical server. A virtualisation software called a hypervisor will partition the physical server or the host machine into several VMs, with each running its own OS. The hypervisor’s abstraction or isolation of the underlying host machine hardware enables the multiple VMs to share the physical server’s resources, such as network bandwidth and memory space (Rouse, 2017; Yasar, 2023)
A Database Server is a type of server that will manage a database system. This is also called a database management system (DBMS). Examples of DBMS include MySQL or SQL Server.
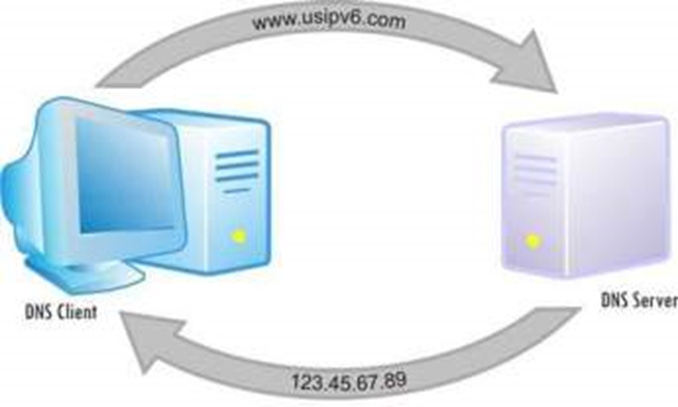
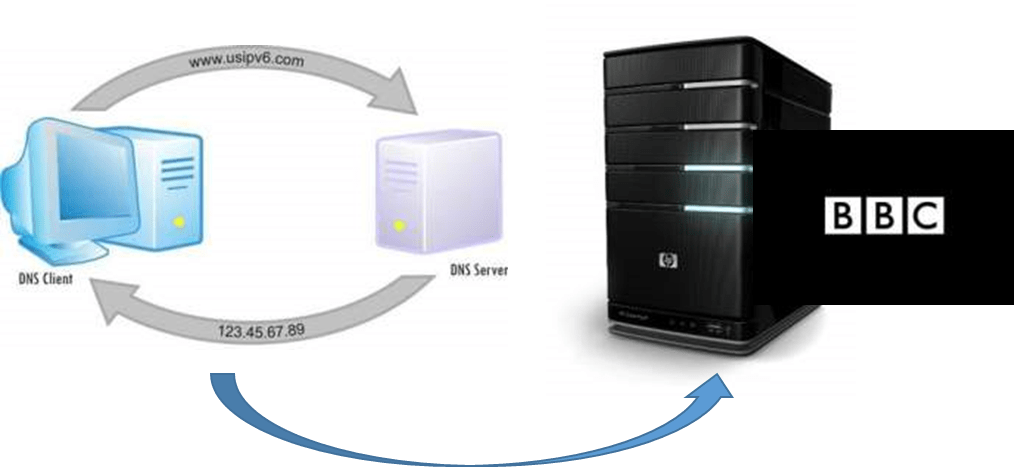
A Domain Name System (DNS) is a distributed database that matches IP addresses to computer system resources. DNS is the system used to find the computer which hosts the website you are looking for. Users would not have to memorise IP addresses. The DNS protocol uses a massive distributed database organised as a directory system of servers to translate domain names into IP addresses.
One example of this is to match an IP address to a human friendly domain name. For example I can access websites in 2 ways:
URL - http://www.bbc.co.uk
IP address - 123.45.67.89
1. You can’t remember the IP address of the computer which hosts the BBC website, so you type in the URL into the browser.
2. The URL is sent to your ISP and they look up the URL in their DNS ‘address book’. They find it and send back to you the websites URL address.
3. Now you can communicate with the computer which hosts the website on the internet, directly.
Another example where a DNS server is used is where a computer system, on joining a network, would query the DNS server for the IP address of other useful computer systems, such as the logon server, which stores the details of all usernames and passwords.
A CD-ROM Server is a type of server that allows all the client stations to obtain data from a CD-ROM disk being used by the CD-ROM server computer (British Computer Society, 2005). A CD-ROM server will often have access to many CD-ROM disks, either from a collection of several CD-ROM players or from a CD-ROM jukebox.
An Internet Server is a type of server that manages access to the Internet for all the users of the network. It is also known as a proxy server
A Blade Server is a compact device containing a computer used to manage and distribute data in a network.
A Policy Server is a security component of a policy-based network that provides authorisation services and facilitates tracking and control of files. Policy servers accept access control requests, process them against a formal set of statements that define how network resources are to be allocated among its clients and returns access control responses.
Why Have Different Servers? Why Not Just Have One?
There are lots of reasons why we have different servers doing different functions rather than every single function under the sun in one single server.
One big reason is security. Think about a DNS that we covered. There are threats to a DNS – that is just DNS, never mind the other types of servers we have covered. One of these threats comes in the form of a subdomain takeover. Subdomain takeovers occur when a bad actor takes control of a subdomain of a target domain and is effectively able to change the records to their liking. This usually happens during the removal process in which the domain owner removes a cloud service, but forgets to remove the DNS pointer. A few things that can be done to prevent a subdomain takeover include:
· Defining a standard process for provisioning and removing hosts
· Creating a detailed inventory of all the domains
· Hosting providers within your organisation
· Updating providers to ensure there are no dangling DNS issues
Email is a relatively open and insecure system that allows people to send messages back and forth with little friction. Spoofed messages are often used by bad actors to get users to install malicious software or give up sensitive information such as passwords, credit card data or wallet seed phrases. Spammers who send fake emails using your legitimate domain could cause users to mark authentic emails from your organisation as spam as well. Spoofing negatively impact your organization’s long term reputation. Spoofing also directly affects the trust users have in your service and technology
Although cloud security providers can protect your organization from DDoS attacks, bad actors can still find the IP address of your origin server. There are a few main ways a hacker can obtain information on your origin services including:
· An application being used with your organisation having a direct link to your origin server and that link being discovered
· Paper trails from certificate transparency records
· Inadvertently disclosing the DNS records on the system
· Train people in your organisation on how to verify whether emails are genuine or not
As with other DNS vulnerability recommendations, implementing a system with best practices is a great way to start. Other suggestions include publishing public websites behind cloud-flare, avoiding exposing test instances of applications to the internet, and generally supporting your developers as much as possible to make this whole process seamless. The DNS vulnerabilities outlined so far have the power to compromise your organisation’s security and sensitive data
However there are a number of ways to spot them whilst mitigating against any potential damage.
DNS poisoning refers to when fake information is entered into the cache of a domain name server. The result is that DNS queries produce incorrect replies thereby sending users to the wrong website. DNS Poisoning works in numerous ways. The Man-in-the-Middle (MTM) Attacks is when the attacker gets between the web browser you are using and the DNS server. They use a tool to alter the information in the cache on your device, as well as the information on the DNS server and get redirected to a malicious site.
DNS Poisoning works in different ways. One such way is the DNS Server Hijack. When hijacking a DNS server, the attacker makes adjustments to the server, causing it to direct users to a malicious site. The fake DNS information causes every user who enters that website’s address to get sent to the fraudulent site. Another way is the DNS Cache Poisoning via Spam. When an attacker uses spam for DNS spoofing attacks, they put the code used for the cache poisoning inside an email. The email will often try to scare users into clicking on the link that ends up launching the DNS poisoning attack.
Data Theft is another threat to the DNS. An attacker can have the user redirected to a phishing website that can collect the user’s private information. When the user enters it, it gets sent to the attacker, who can then use it or sell it to another criminal
Malware Infection is yet another threat to a DNS. A cyber-criminal may have the user sent to a website that infects their computer with malware. This can be done through drive-by downloads. They automatically put the malware on the user’s system or through a malicious link on the site that installs malware, such as a Trojan virus or a botnet.
In relation to halted security updates, an attacker can spoof an internet security provider’s site. When the computer attempts to visit the site to update its security, it will be sent to the wrong one. As a result, it doesn’t get the security update it needs, leaving it exposed to attacks. Censorship can be executed via manipulation of the DNS as well. For instance, in China, the government changes the DNS to make sure only approved websites can be viewed within China.
Security isn’t the only reason.
· Hardware Failure – If one of your server’s hardware should malfunction or be ruined in any way, you’ll still be able to access your database and important information stored on a separate server (Paperless Environments, 2023).
· Overall Performance – Splitting servers will help to avoid database clustering; with less information on each individual server, your overall system will continue to move much more smoothly (Paperless Environments, 2023).
· Physical Speed – The physical location of a server matters. If you have a large company that spans across the country or even overseas, you will benefit from having multiple servers interspersed to ensure uniform ease of use (Paperless Environments, 2023).
· Multiple Users – It is extremely beneficial to host all of the data on one server and then distribute the front-end workstations to others so that everyone can access and edit the same information without getting locked out or overwriting one another (Paperless Environments, 2023).
· Cost Efficiency – It is less expensive each month than constantly adding resources to one server. However, fewer servers mean lower hardware, software, and management costs (Hannifin, 2010; William, 2019).
· Reduce Dependability – Having separate servers means reduced dependability of the resources of each other.
· Improve Database Functions – Having a separate database server is more suitable for a web-based business.
· Effective Resource Monitoring – Having multiple servers allows for effective resource monitoring, which results in better performance and efficiency.
These are just some of the reasons why we have separate servers rather than having everything on one single server.
Reference List
British Computer Society. Glossary Working Party, (2005) The BCS Glossary of ICT and Computing Terms Eleventh Edition Harlow, Essex: Pearson Education Limited
Hannifin, D. (2010) Microsoft Windows Server 2008 R2 administrator's reference: the administrator's essential reference Oxford: Syngress Publishing
Paperless Environments (2023) ‘5 Benefits of Splitting Servers’ Available at: https://paperlessenvironments.com/5-benefits-of-splitting-servers/#:~:text=Overall%20Performance%20%E2%80%93%20Splitting%20servers%20will,location%20of%20a%20server%20matters (Date Accessed: 28/06/2023)
Piper, T. (2016) Cambridge International AS and A Level Computer Science Revision Guide Cambridge: Cambridge University Press
Posey, B. (2023) ‘What is a Server?’ Tech Target Available at: https://www.techtarget.com/whatis/definition/server#:~:text=A%20server%20is%20a%20computer,referred%20to%20as%20a%20server (Date Accessed: 30/06/2023)
Rouse, M. (2017) ‘Virtual Server’ Techopedia 18th January Available at: https://www.techopedia.com/definition/27139/virtual-server (Date Accessed: 05/07/2023)
William, J. (2019) ‘6 Reasons Why You Should Start Using A Multi-Server Environment’ Temok 7th November Available at: https://www.temok.com/blog/multi-server-environment/ (Date Accessed: 05/07/2023)
Yasar, K. (2023) ‘virtual server’ Tech Target Available at: https://www.techtarget.com/searchnetworking/definition/virtual-server (Date Accessed: 05/07/2023)
Any questions please drop a comment below. If you like the sound of my work, please share and subscribe!